Protection Without Compromise
High Assurance Virtual Systems
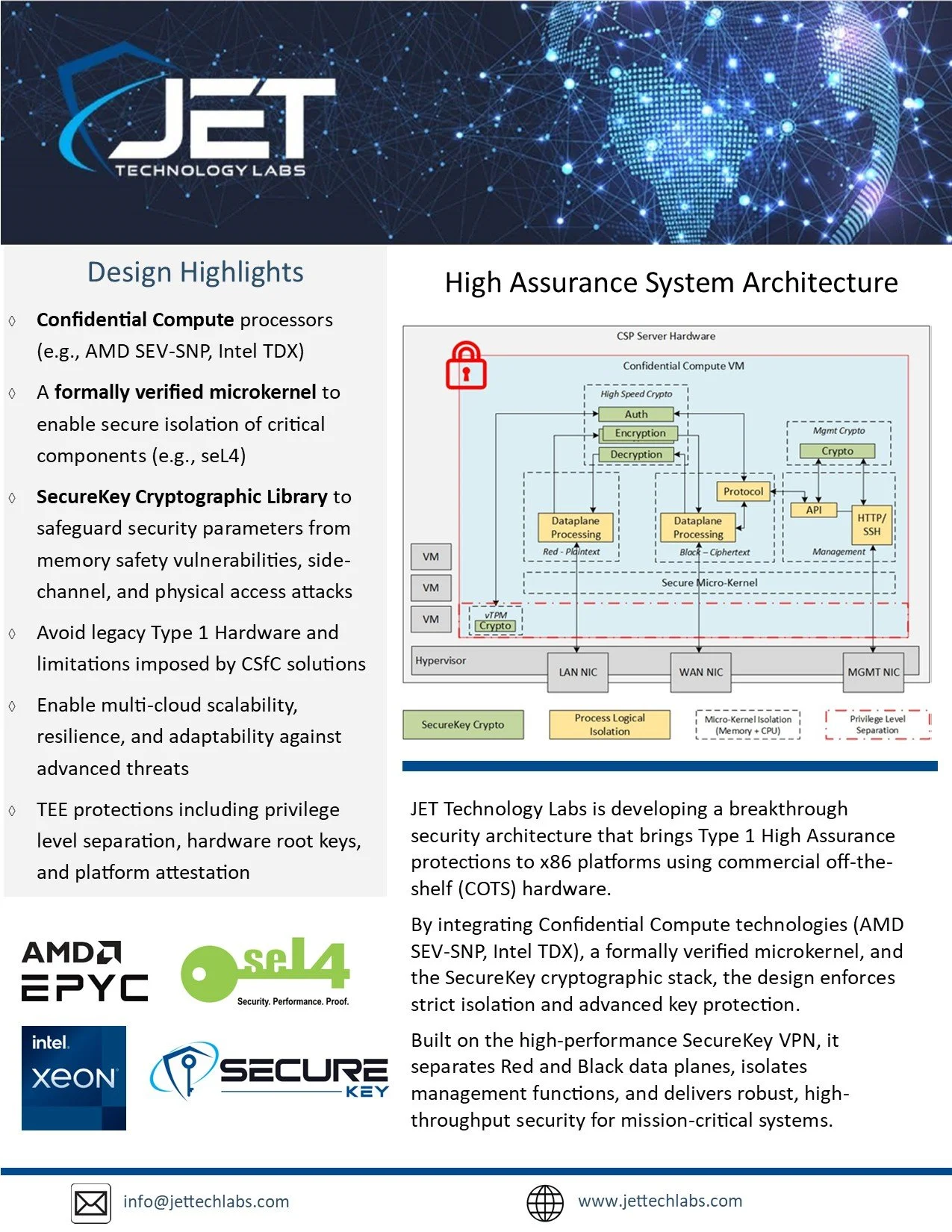
Our state-of-the-art concept security architecture enables next-generation High Assurance virtual solutions. By seamlessly integrating Confidential Computing hardware protections, a formally verified secure microkernel, and the advanced cryptographic capabilities of SecureKey software, we are building a virtual environment to run High Assurance workloads including encryption, key management, and cross domain solutions. This powerful architecture ensures unparalleled protection on commercial off the shelf hardware, safeguarding critical assets against evolving threats.
🔐 Advanced Security for SD-WAN and Zero Trust
SecureKey provides the cryptographic foundation for next-generation SD-WAN and Zero Trust solutions. By combining high-assurance encryption with Confidential Compute protections, SecureKey ensures that security and performance scale together—enabling secure, policy-driven access across cloud, edge, and hybrid environments.
🛡️Security Threats, Neutralized
By combining the power of Confidential Compute hardware with our breakthrough SecureKey cryptographic software, we eliminate advanced threats at their source—ensuring uncompromised security, even in the most hostile environments.
-
Purposeful security design employs a multi-faceted approach to address Zero-Day vulnerabilities in both software and hardware through a layered Defense-in-Depth strategy. This involves using Hardware isolated Trusted Execution Environments (TEEs) along with robust software protections to enhance overall security.
To further mitigate N-Day attacks, design practices are rooted in proactive security measures while firmware and software updates are deployed, safeguarding against exploitation and fostering a resilient system architecture. This comprehensive security framework not only anticipates potential threats but also provides mechanisms for timely response and remediation.
-
Purposeful security design focuses on mitigating side channel attacks by implementing various strategies to protect memory caches, which are frequently targeted by attackers. By isolating processor resources, this approach ensures that sensitive information is safeguarded during computation. Effective isolation minimizes the risk of unauthorized access and manipulation, enhancing overall system resilience against potential exploits. This layered defense is crucial for maintaining the integrity and confidentiality of data within modern computing environments.
-
The framework enforces high security algorithms, modes, and settings such as CNSA algorithms and modes. Cryptographically strong measures are used to validate settings and configurations and all encryption protocols adhere to established security standards. Robust key management practices are used to safeguard cryptographic keys at all times and multi-factor authentication enhance overall system integrity and protect sensitive data from unauthorized access.
-
Silicon rooted TEE security protections offer a robust layer of security by ensuring that both user and device identities are authenticated with high confidence. This approach leverages trusted execution environments to safeguard sensitive operations and data against potential threats.
The active intrusion detection and prevention measures further strengthen this security framework. By continuously monitoring for anomalies and unauthorized activities, these measures effectively mitigate risks, ensuring that only verified users and devices can access critical resources. This combination of TEE and proactive defense not only fortifies the security posture but also promotes a resilient environment equipped to adapt to evolving threats.
-
Our secure-by-design architecture empowers companies to break free from the endless cycle of security patches by delivering robust, multi-layered protection against software attacks and vulnerabilities. By integrating hardware and software enforced safeguards for critical components such as vTPM, data plane cryptography, and management cryptography, our architecture minimizes the impact of software bugs—even within the operating system. This dramatically reduces the need for frequent critical security patches, ensuring a more resilient and secure system.